Some terms
Some terms you’d need to know before we start:
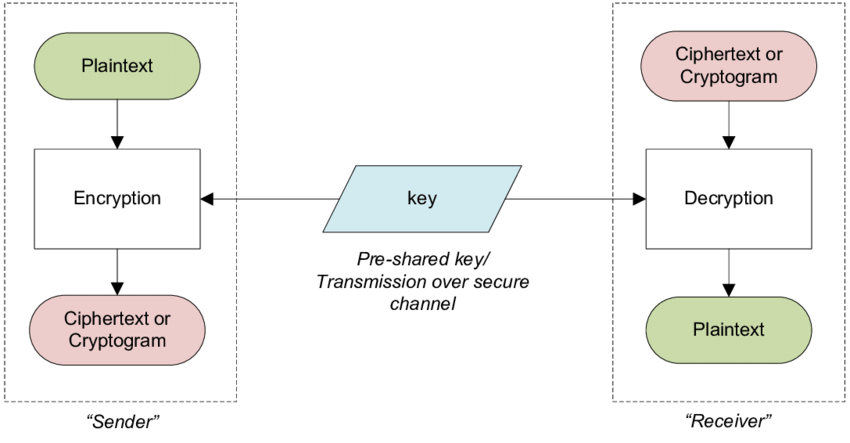
- Plaintext: The original message that you want to encrypt.
- Ciphertext: The encrypted message.
- Key: The secret value that is used to encrypt and decrypt the message.
What is encryption?
Encryption is the process of converting plaintext into ciphertext. This means taking normal text like “Hello World” and turning into something that looks like complete gibberish. The more gibberish it looks like, the better. Unlike hashing, encryption is reversible, meaning you can turn the gibberish back into the original text and unlike encoding, encryption requires a key to decrypt the message.
Substitution Cipher
One of the most basic forms of encryption is the substitution cipher. As the name suggests this is where you substitute one letter for another. For example, you could replace every “A” with a “Z”, every “B” with a “Y”, and so on.
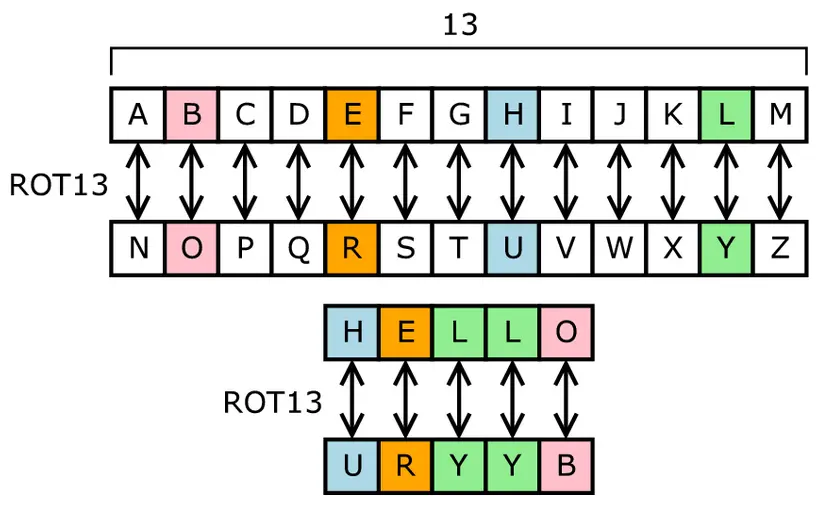
For example, lets use a rotation of 23 (also known as ROT23)
A = X, B = Y, C = Z, D = A, …
Plaintext: THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG
Ciphertext: QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD
Have a look at Caesar Cipher↗ as an example of a substitution cipher.
Substitution just means replacing one thing with another. In this case, we’re replacing one letter with another. You could replace a letter with multiple letters, or even a symbol.
Symmetric Encryption
This type of encryption uses the same key to encrypt and decrypt the message (symetric means same). This doesn’t require a lot of computational power and is generally faster than asymmetric encryption.
The problem is that if the key is compromised, then the attacker can decrypt all the messages. You’d also need a secure way to share the key with the other party.
Some popular symmetric encryption algorithms are:
- AES (Advanced Encryption Standard): This is the most widely used encryption algorithm. It is used by the US government and is considered to be very secure.
- ChaCha20: This is an authenticated encryption with additional data (AEAD) algorithm, that combines the ChaCha20 stream cipher with the Poly1305 message authentication code.
Asymmetric Encryption
Also known as public-key encryption, this type of encryption uses two keys: a public key and a private key. The public key is used to encrypt the message and the private key is used to decrypt the message.
This is difficult for some people to understand, try this: Imagine a locked mailbox, it has a lock needed to open it to put a letter in and a different lock to open it to take a letter out. The PUBLIC facing part of the mailbox is the lock that anyone can use to put a letter in, this is the public key (something that anyone can just have). The PRIVATE part of the mailbox is the lock that only the owner of the mailbox can use to take a letter out, this is the private key (something that must never be shared).
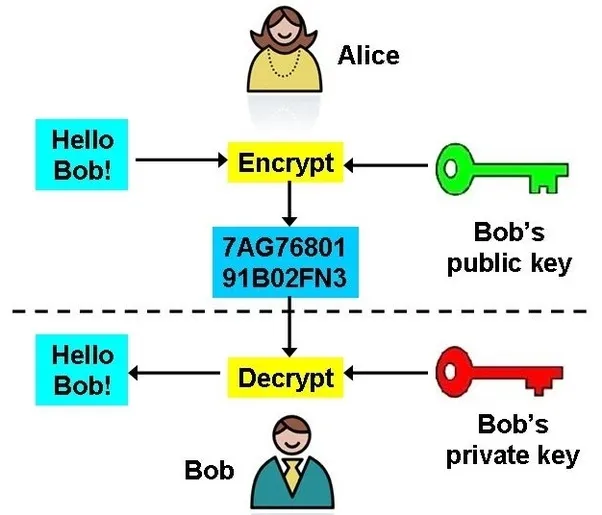
In the driagram above, Alice wants to send a message to Bob. Bob has a public key and a private key. Alice uses Bob’s public key to encrypt the message and sends it to Bob. Bob then uses his private key to decrypt the message.
⚠️Never Share Your Private Key
It is called a private key for a reason, this one should in no case be published anywhere or accessable to anyone. You are free to publish and spread your public key though.
Some popular asymmetric encryption algorithms are:
- RSA (Rivest-Shamir-Adleman): This is the most widely used asymmetric encryption algorithm. It is used by the US government and is considered to be very secure.
- PGP (Pretty Good Privacy): This is a program that uses asymmetric encryption to secure email communications. It is considered to be very secure.